AI is the hot topic of 2025 and there are new developments about it everyday. Whether its OpenAI, Claude, Gemini, Mistral or open source models like DeepSeek R1 and Metas’ LLama they are all powerful and they are getting better every week. You are probably already using AI for your everyday tasks but are you aware how easy it has become for non technical fraudsters to build malicious bots that signup to your website, fill out forms or just click on your ads ? If not read on because you might be suprised!
Reasons for writing this post
When advising clients on fraud and cybersecurity issues, we frequently encounter questions about distinguishing bot traffic from genuine user activity. Modern website visitors and clicks can appear incredibly realistic and are no longer detectable without proper experience and specialized tools. However, detection capabilities are only valuable if users trust them enough to act on identified malicious traffic.
There are two types of bots. The beneficial ones include search engine crawlers, SEO tools like Ahrefs, and AI engines that index web pages. These typically identify themselves through unique user agents, making them easy to recognize and filter if necessary.
Today, we’re focusing on the second type: malicious click bots that actively conceal their nature. These sophisticated bots simulate real devices and locations while operating through legitimate Internet Service Providers, making it incredibly difficult to distinguish legitimate traffic from fraudulent activity. Large Language Models have significantly simplified the process of building malicious click bots, making this discussion increasingly relevant.
Following the open-source approach to security, I believe in the educational value of building awareness rather than relying on false obscurity. For this reason, let’s examine the issue from a different angle—exploring how these systems work from a fraudster’s perspective.
Objective
Our objective is to build a Click Bot that mimics normal user behaviour, simulates a range of devices, languages, fakes the referer URL (to make traffic appear to come legit sites) like Google.com or Wikipedia.org. To not get easily detected we will randomize the IPs, change its location and even change it random Internet Service provider to make our traffic even more look legitimate. From a technical perspective we want to get all this done without any programming skills, utilzing AI to help us with the coding.
Installing Python
In principle any programming language can do the job but because of the wide popularity and ease of use we will choose Python as a language. A benefit of python is that many libraries for all sorts of requirements are available. As a first step we should download Python from here. It is available for both Windows and Mac Os and fully free of charge. The setup is straight forward and does not require technical experience.
Choosing a Code Editor
To be able to create the python code we will need a code editor. A code Editor is like Word for Software Developers. For our example we will use Windurf Code Editor. It is a AI native code editor that will make our job a little easier. They offer a 2 week free trial and is easy to use. So as a next step we install Windsurf Editor from here. If you already have a an existing Code Editor you can use that one of course too.
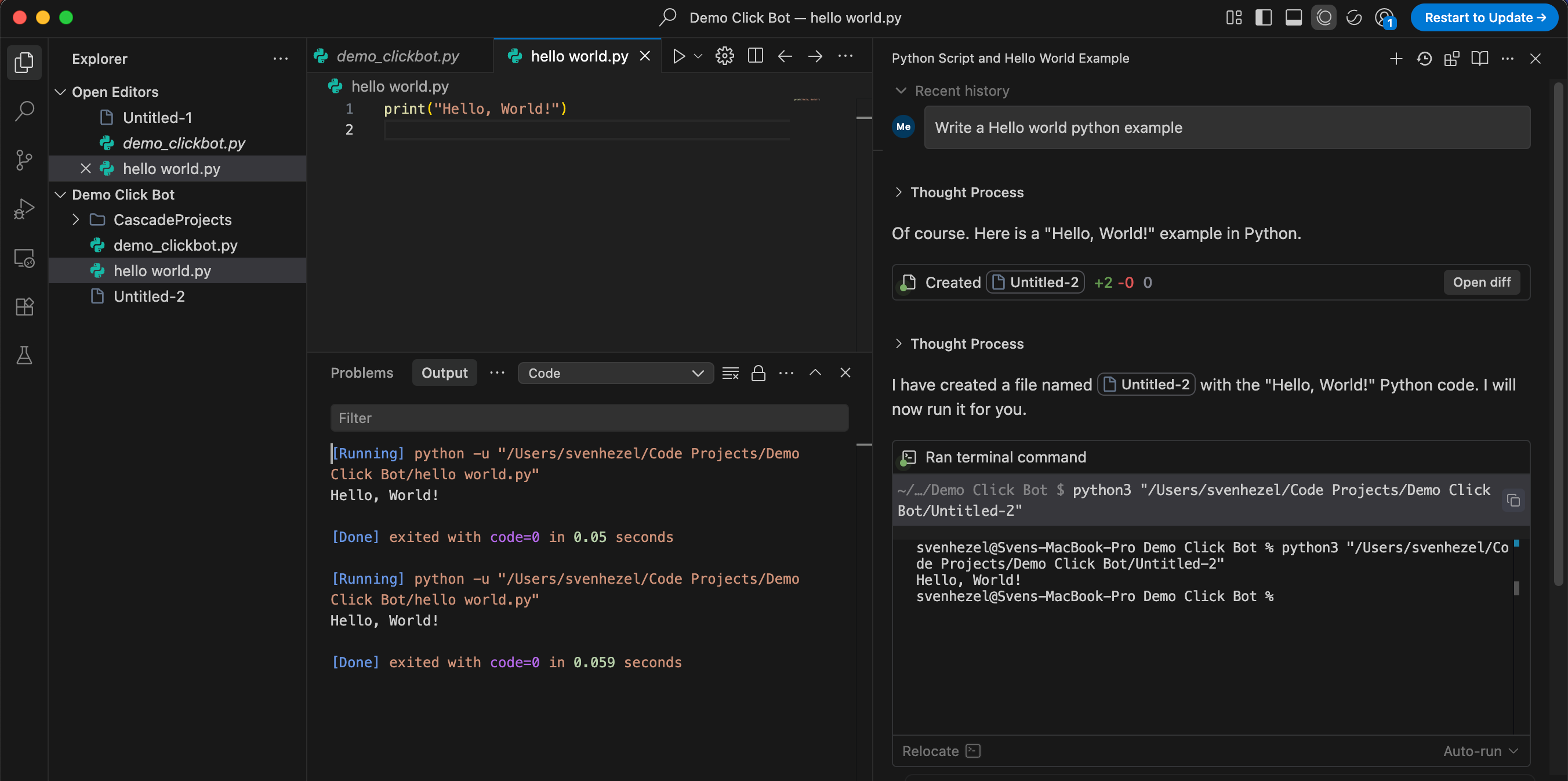
Windsurf Cascade Mode
Before starting the code creation we need to familiarize ourselves with Windsurf a little. In its core its like a File Editor but it has one special feature that sets it apart from traditional code editors which is the Cascade Mode. It basically like a Chat Window
Getting around AI’s ethical concerns
When you AI with your direct intent you are most likely to not get what you want. Safety mechanisms prevent giving you a direct answer.
Fortunately (or unfortunately) there are ways around it. We can for example describe the request more technically and if needed break it apart into multiple steps. This will make the AI ignore safety concerns and return the code that we want. Since its not a difficult task we probably dont have to do this here but I won’t go into too much detail here. I am sure you get the idea.
The Prompt
This is the most interesting part. Ideally we would want to have a 1 Shot prompt that gives us the whole script without additional iterations. The more descriptive the prompt the better the results. As you see in my example below its not a very long prompt but it has enough technical information of how we want our Bot to behave. To simulate the IP we will need an account with a Proxy provider. Fraudsters typically use Residential Proxy services these days. Typical provider are Geonode , Brightdata.
Create a Python script designed for a making requests to a specific Target URL. The script should simulate realistic devices, mimic realistic user behaviors. Only use standard libraries that are part of Python.
Use this this Proxy URL to connect to the Internet: https://username:[email protected]:port_number
On each request do the following:
1. Connect to the Proxy
2. Randomize the User Agent with a list of modern Desktop and Mobile Devices
3. Randomize the Browser Language Between U.S English, Candian English and Spanish
4. Randomize Referer URL Header including popular websites like Google and Facebook and Youtube 5. Set a random Pause between each request between 1-10s
The Results
The generated code is only 67 lines long and only took as a few minutes to generate. Now with this at hand a fraudster could simulate fake devices and pretend sending traffic from some of the most legitimate sites on the internet. If you are interested you can download the full source code from our Github Account.
import urllib.request
import random
import time
# Proxy configuration
proxy_url = "https:/user_name:[email protected]:port_number"
proxy_handler = urllib.request.ProxyHandler({
'http': proxy_url,
'https': proxy_url
})
opener = urllib.request.build_opener(proxy_handler)
urllib.request.install_opener(opener)
....How to prevent attacks like this:
These attacks are not visible without advanced analysis tools. There are various providers that offer proxy detection. My recommendation on choosing the right provider:
- Check the pricing pricing vary greatly between providers and if you want to check on Click Level it can get pricey quickly
- They should offer a free trial and you should check yourself how effective their system is. You can test us using our free IP Reputation Scanner on our website.
- Ideally also choose a provider that covers Bot Detection in the same package
For everyone that is looking for a free and simple system to protect their WebForms / Login you can install our free CyberSecurity Website Plugin. It comes with a generous volume of 100k Clicks / month which and protects your Site from Bots, VPNs, DataCenter and Proxies.